How to spin up bastion
Introduction
Bastion is a jump server (or gateway server) that gives access to Instances within a private network using the SSH protocol.
Bastion is a secure intermediary server where Monitor Space Hazards system administrators login first via SSH before getting to access the different components. The purpose of having the SSH bastion host is to improve security and consolidate SSH user activities to a single point hence better security and accountability.
Spinning up bastion
Go to Instances, make sure the
bastion-host-for-prodis checked and select Start instance under Instance state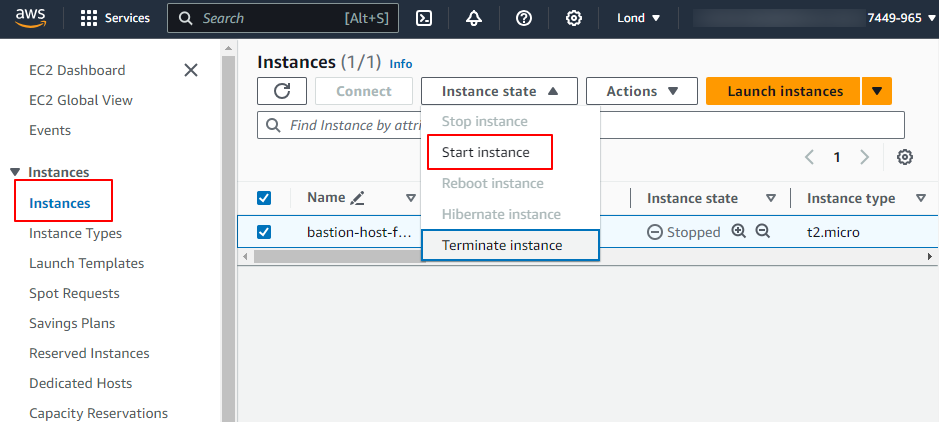
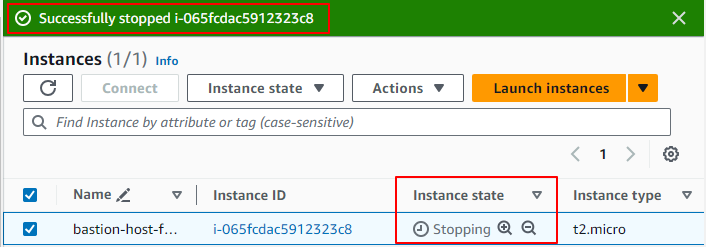
You will be notified at the top to let you know the bastion host has started successfully and the Public IP address will be displayed.
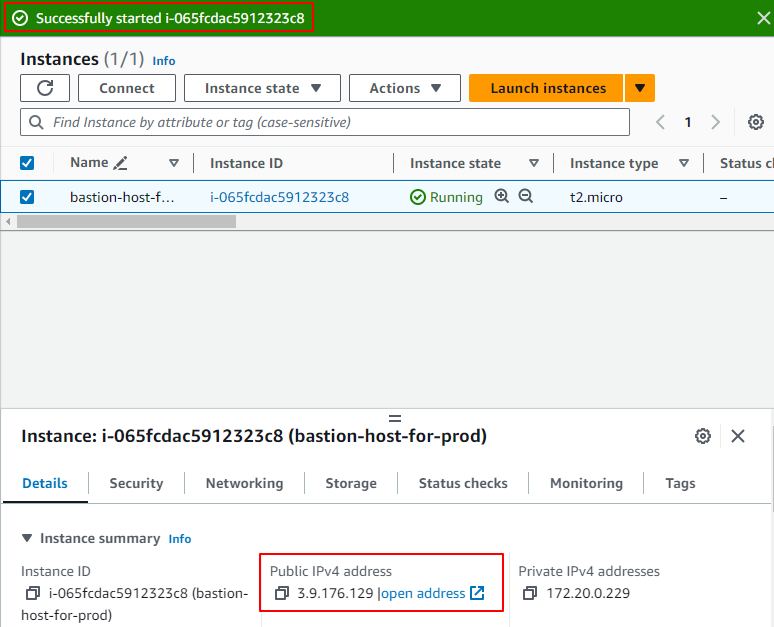
You can then connect via SSH using ec2-user@
to connect to the production database. An example command might be: psql -U msh -h aurora-cluster-for-prod.cluster-czgkvdogsvmn.eu-west-2.rds.amazonaws.com -p 5432 -d mshThe password can be found in Secrets Manager. For the manual intervention on Database there is also a username
postgres. The password for this is also in Secrets Manager.Once you have finished, shutdown the host by selecting Stop instance so unnecessary costs are not incurred.